Introduction
Misc was certainly intresting lol. These will also be very brief. However I’m sure you’ll be intrested in this misc/golf-hardester writeup by Lunbun. btw disclaimer, smiley did not play this ctf as a whole team, any writeups by smashmaster and HELLOPERSON should be attributed to the team participating as “Les Amateurs”.
misc/lost
tjctf{uppercasecode} 99% of the work was Orz Larry playing ctf on phone during vacation.
- UST is the middle of the word “Houston”, the image shows "" which is Spanish for “Gate” as well as a date of August 13, 2023.
- this website allows us to find all arriving flights at the one Houston airport that actually does international flights
- Orz Larry realizes we go to the next day and tries all the Spanish speaking countries
misc/linkedout-recon
someone has been climbing the corporate ladder a little too quickly… you’ve been given access to a single document. everything you need is public - if you know where to look. your mission should you choose to accept it: uncover what’s hidden in plain sight.
NOTE: The pdf metadata shows the file was created by Andrew Liu but there was a clarification over discord to not osint that.
There’s actually a lot of fake info in this chal especially about DEF CON. One strat I used to work around this was searching up the “Blue and White Professional Corporate Resume” template in Canva the author stole which was the title of the pdf according to exiftool to diff with the original template.
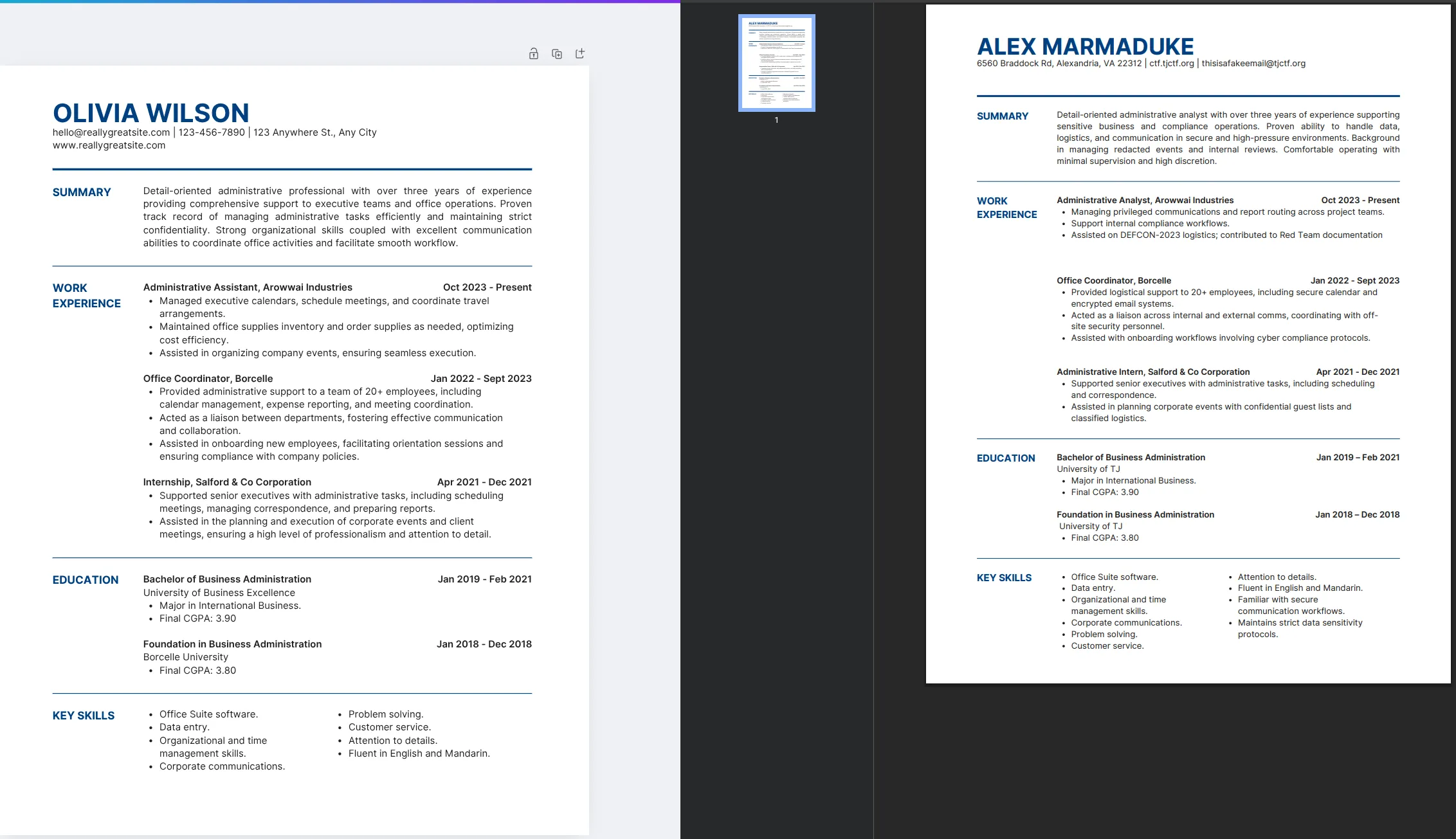
Seems like all the Cyber related stuff was added in and the business names are all placeholders. Searching up the name on DuckDuckGo finds us a GitHub profile of a user which was recently created which tells us we’re on the right track for OSINTing someone related to the ctf (their profile even mentions CTF). There’s a lot of yap in their profile markdown but their only gist basically has the same Notion link we want to follow. The notion is also a bit of stuff that doesn’t make sense when cross referencing actually DEF CON material. I’m not surprised given that almost no one references DEFCON by year like “DEFCON 2023”. The Notion leads to this password protected zip on Google Drive.
How fitting. If you participated in amateursCTF 2023, you might have remebered the guessCTF chal used password protected zips to make the multiple levels of the chal. guessCTF was not really meant to be solved but during the CTF a team cleverly deduced that because ZipCrypto was being used for the password protection of the zip, you could use bkcrack and known plaintext to find the contents of the zip through a known plaintext attack.
With that said, whenever we see a password protected zip, we should always try to find what kinds of cyrpto it is using.
raymond@nobara:/home/raymond/Downloads$ 7z l -slt protected.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,<lol it puts your cpu specs here> (A40F41),ASM,AES-NI)
Scanning the drive for archives:1 file, 356873 bytes (349 KiB)
Listing archive: protected.zip
--Path = protected.zipType = zipPhysical Size = 356873
----------Path = encoded.pngFolder = -Size = 356705Packed Size = 356717Modified = 2025-06-07 08:43:07Created =Accessed =Attributes = AEncrypted = +Comment =CRC = DC0D4039iZ`Method = ZipCrypto StoreHost OS = FATVersion = 20Volume Index = 0So we see this zip is likely vulnerable because it uses ZipCrypto and because “Store” is being used, there’s no actual compression being done.
The file in question is a png so we can likely rely on it having a predictable header for the 12ish bytes bkcrack needs. I just took a random png and did head -c 12 > header.png because bkcrack expects the known plaintext to be in it’s on file.
smashmaster0045@kali-thing:~/ohlarry/tjcrack/bkcrack-1.7.1-Linux$ ./bkcrack -C protected.zip -c encoded.png -p header.png -d encoded_decoded.pngbkcrack 1.7.1 - 2024-12-21[00:21:04] Z reduction using 9 bytes of known plaintext100.0 % (9 / 9)[00:21:04] Attack on 742655 Z values at index 6Keys: ceb44b48 d0bef198 9bd350f729.7 % (220330 / 742655)Found a solution. Stopping.You may resume the attack with the option: --continue-attack 220330[00:21:36] Keysceb44b48 d0bef198 9bd350f7[00:21:36] Writing deciphered data encoded_decoded.pngWrote deciphered data (not compressed).We can also recover the original password from bkcrack.
smashmaster0045@kali-thing:~/ohlarry/tjcrack/bkcrack-1.7.1-Linux$ ./bkcrack -k ceb44b48 d0bef198 9bd350f7 --bruteforce ?b --length 0..9bkcrack 1.7.1 - 2024-12-21[00:22:30] Recovering passwordlength 0-6...length 7...length 8...Password: princessFound a solution. Stopping.[00:22:30] Passwordas bytes: 70 72 69 6e 63 65 73 73as text: princessFrom here it becomes clear that we were actually meant to do brute force against a small wordlist but I guess this works too and is less guessy. The extracted png is here:
It doesn’t make sense but it turns out if you just zsteg the png you get the flag, which…might have been very guessable.
smashmaster0045@kali-thing:~/ohlarry/tjcrack/bkcrack-1.7.1-Linux$ zsteg encoded_decoded.pngb1,rgb,lsb,xy .. text: "29:marmaduke:tjctf{linkedin_out}"b2,r,lsb,xy .. text: "QUeVAUie"b2,bgr,lsb,xy .. text: "M\r&MIBMI"b2,rgba,lsb,xy .. text: "k[7sssS'o'"b3,g,lsb,xy .. text: "Z%DJ) J%$"b3,g,msb,xy .. text: "mI\"-R %\n"b3,b,msb,xy .. file: OpenPGP Secret Keyb3,rgb,lsb,xy .. file: Tower/XP rel 3 objectb4,b,msb,xy .. text: "]=S=Y=U]Y"